
Click
on the headings for brief
details about the services that G2Solutions offers.
For additional information,
or to arrange a demonstration, please email us at g2info@g2sinc.com.
- Secure Record Receipt
- Data Validation
- Record Forwarding
- Web-based Data Collection and Scheduling Service
- Web-based Management and Financial Reporting
- Transaction Summaries via Email
- Server Firewall and Anti-Virus Protection
Secure
Record Receipt
G2Solutions provides a Secure Simple
Mail Transport Protocol (SMTP) Server accessible via the Internet for
the receiving of NIST records. Security is provided via the Secure Sockets
Layer/Transport Layer Security (SSL/TSL) architecture, utilizing 128-bit
secure DSA encryption, backed by a VeriSign Certificate of Authenticity.
Alternatively, G2Solutions can make the SMTP Server available via Secure
Internet Virtual Private Network (VPN) using 128-bit TripleDES encryption,
or any proprietary VPN that utilizes IPSEC.
Data Validation
While all Livescan Systems are certified
for NIST record creation and editing, G2Solutions offers data integrity
checking, and customized validation of field data that may not always
be strictly defined in the EFTS. This is particularly important where
two or more fields' data is interrelated and requires cross checking
to ensure consistency of the values provided. With data errors accounting
for a large number of rejected records, G2Solutions is committed to providing
every possible means of reducing this number, thereby saving applicants,
submitters and agencies bandwidth, time, and money. Records found to
contain erroneous data generate an alert which is then sent immediately
to the submitter for correction. This email typically will be sent within
30 seconds of a record being received, enabling the submitter to correct
and re-submit the record while the Applicant is still present.
Record
Forwarding
After being received and validated,
record data is examined to determine, based upon customer defined rules,
where the transaction is to be routed. For submitters who wish to capture
records for a variety of Controlling Agencies, this feature allows them
to have records sent to agencies such as the California Department of
Justice (DOJ) via the Private Applicant Network (PAN), the California
Bureau of Security and Investigative Services (BSIS) via Internet Virtual
Private Network (VPN), the Federal Bureau of Investigations (FBI) via
the Integrated Automated Fingerprint Identification System (IAFIS), the
American Banking Association (ABA), the New York Clearing House, and
the National Airline Transportation Association (NATA) just to name a
few.
Record data such as Type of Transaction
(TOT, 1.04), Originating Agency Identifier (ORI, 1.08), Destination Agency
Identifier (DAI, 1.07), Controlling Agency Identifier (CRI, 2.073), and
any other tag field contained in the record can serve as criteria for
routing rules. Using this approach, it is possible for a Private Patrol
Operator in the State of California to send Security Guard Applicant
Fingerprint checks to the BSIS via the Internet VPN, and all other applicant
fingerprints directly to DOJ via the Private Applicant Network automatically,
based upon the California EFTS Type of Application (2.400) tag field
set. The following diagram illustrates this work flow:
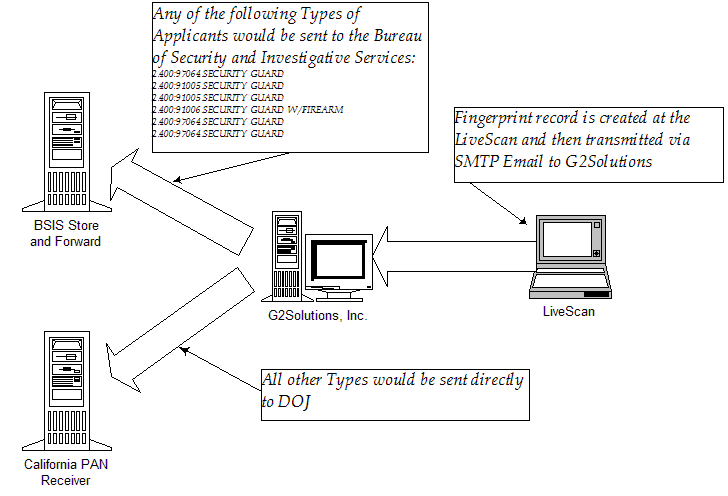
Fig. 1 – Example Work flow for Security
Guard vs Non-Security Guard Routing
Web-based Data Collection and Scheduling Service
As an option to the standard transaction
routing service, G2Solutions also offers
customers and their clients the convenience of online data entry and
appointment scheduling. Applicants may, at their option, create an account
with G2Solutions that stores
all of their employment information. This information is then used when
the Applicant needs to schedule an appointment to have fingerprints taken,
selecting a date and time, and adding the type of application, and employer
information. On the date of the appointment, the record is sent to the
LiveScan scheduled for capture, and when the applicant arrives only the
fingerprints themselves need to be taken.
This account is free to the applicants who, depending on the type of job and security requirements, may have need of several sets of fingerprints, one for each employer. Submitters pay a nominal fee per transaction in addition to the basic service fee.
By using this architecture, submitters can save time, resources, and eliminate transcription errors. In addition, no matter how many times an applicant applies for various positions, the personal data received will always be the same.
Web-based Management and Financial Reporting
Web based reporting is an optional
tool available exclusively to submitters for the purpose of tracking
throughput, averages, trends, and cross-checking fees collected. Utilizing
an Ad Hoc interface, very creative summary and detail reports may be
produced, from total transactions and fees collected for a given quarter,
to the average monthly number of Armed Security Guards fingerprinted
during the past twelve months. These reports can be viewed online, or
saved to Adobe PDF for storage, printing, emailing, and later retrieval.
Submitters pay a nominal additional fee per transaction for this optional
service.
Transaction Summaries via Email
An included
service within the Basic Services, customers can choose to have daily,
weekly, monthly, quarterly, and/or annual summary reports emailed to
themselves. These transaction summaries are subtotaled by Submission
Destination (e.g.
– California DOJ and California BSIS), Type of Applicant, and fees collected.
The reports also include a grand total for the period covered. All information
emailed can be viewed online using the optional Web based reporting tool.
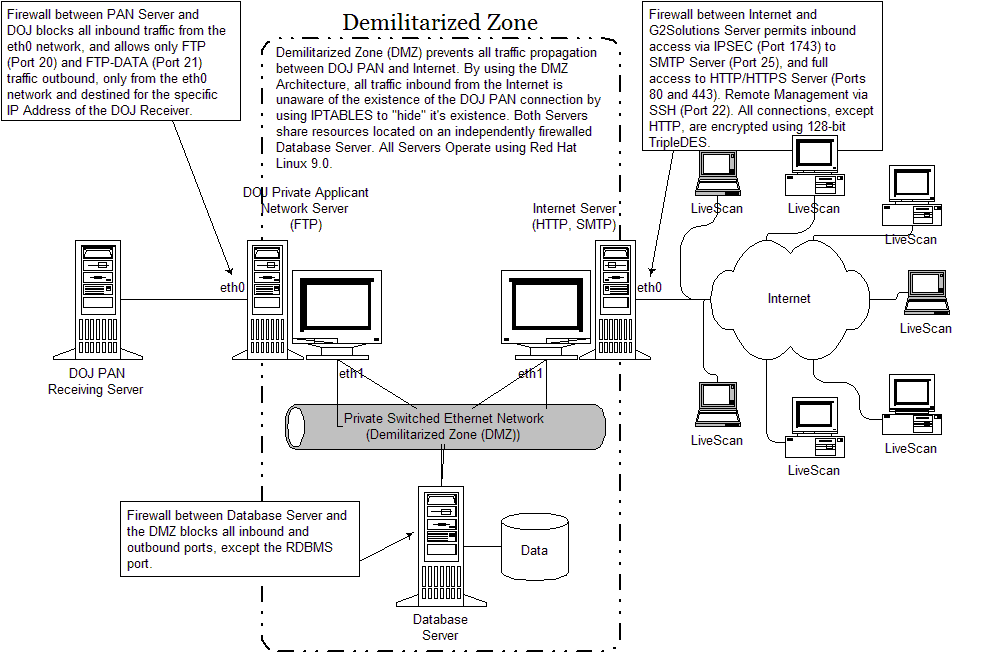
Server Firewall and Anti-Virus Protection
G2Solutions employs multiple servers
for receiving, processing, and forwarding transactions. The Web and Email
Server is the only direct link to the Internet, and is then internally
firewalled and connected to a private Demilitarized Zone (DMZ) Network.
Using Linux and IPTables, access through the firewall is strictly controlled
by port and IP address. While all transactions received will come from
the Internet via Secure SMTP, only those transactions destined for submissions
services available via the Internet, such as the California BSIS, will
be processed by this server. Transactions destined for the California
DOJ PAN, as an example of a Private Submissions Network, will be processed
by a dedicated server connected to the DMZ network internally and externally
via frame relay leased line to DOJ. By isolating this server, and eliminating
any direct link to the Internet, it is possible with IPTables to ensure
zero percent packet propagation from the Internet to the DOJ PAN, and
vice versa, while at the same time minimizing network latency.
As an added measure, unfortunately
necessary in these times, G2Solutions also employees
a very sophisticated Automated Lightweight Intrusion Detection System
(ALIDS). This system continually monitors activity on all network interfaces
for suspicious traffic and generates email, Cellular SMS, and/or pager
alerts immediately upon detection of an intrusion attempt. Working in
concert with the IPTables firewall, the ALIDS System will automatically
block all access from any IP address suspected of launching an attack,
gather all available information about the source, and forward this information
to several Federal Agencies, including the United States Computer Emergency
Response Team (http://www.cert.org)
located at Carnegie Mellon University.
Once done, this IP address will
remain blocked for 90 days, or until manually removed by one of our Network
Administrators. As an added measure of security, if an attack exceeds
a predetermined threshold of source IP's, such as in the case of a Distributed
Denial of Service (DDoS) attack, the Internet connected Server will isolate
itself from the DMZ private network by downing and disabling the internal
interface, thus ensuring the integrity of systems, networks, and data
to which G2Solutions has access.
